Configuring a 3rd Party VPN service on TrueNAS
3 minute read.
Last Modified 2022-12-07 14:12 -0500TrueNAS includes the ability to run OpenVPN. This is a short tutorial to configure the OpenVPN client on TrueNAS 12.0.
Many VPN services are provided by 3rd parties that are unaffiliated with iXsystems. Please verify compatibility and pricing with your provider before integrating with TrueNAS.
Prerequisite: An OpenVPN server running with a similar configuration to these configuration file settings:
-
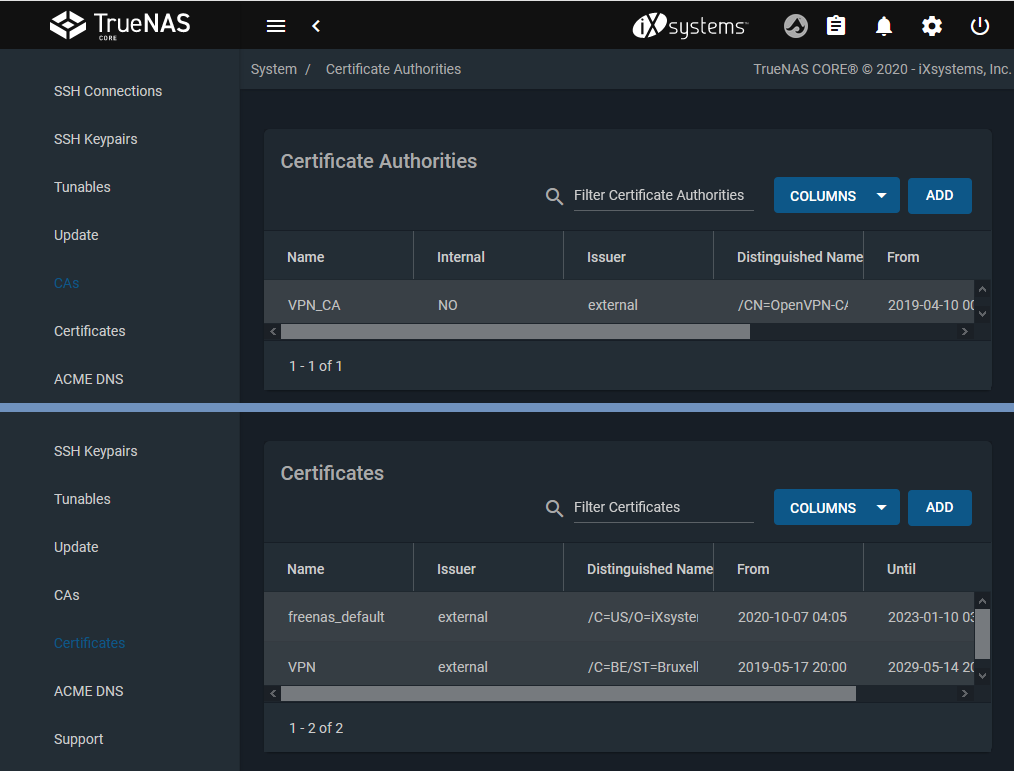
Open System > CA.
-
Add a new certificate authority.
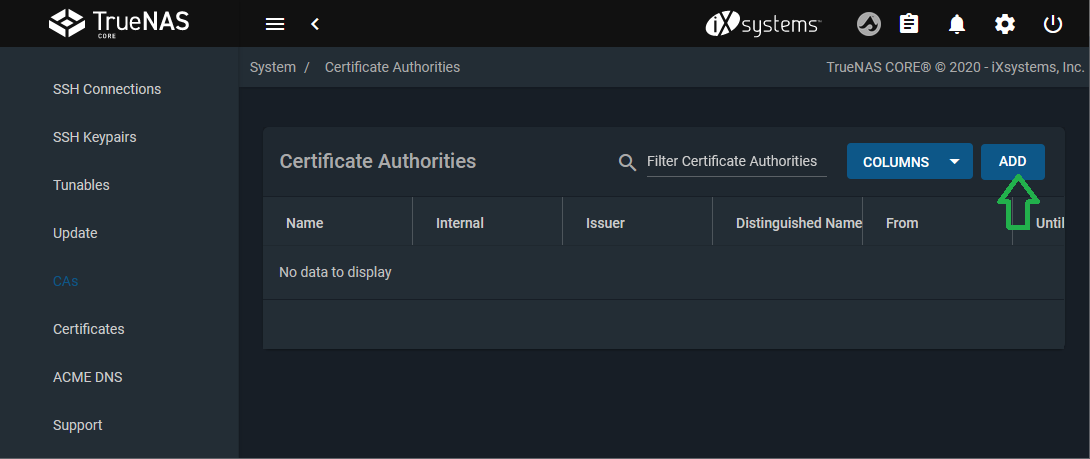
Give it a name (example:
VPN_CA) and select Import CA as the Type.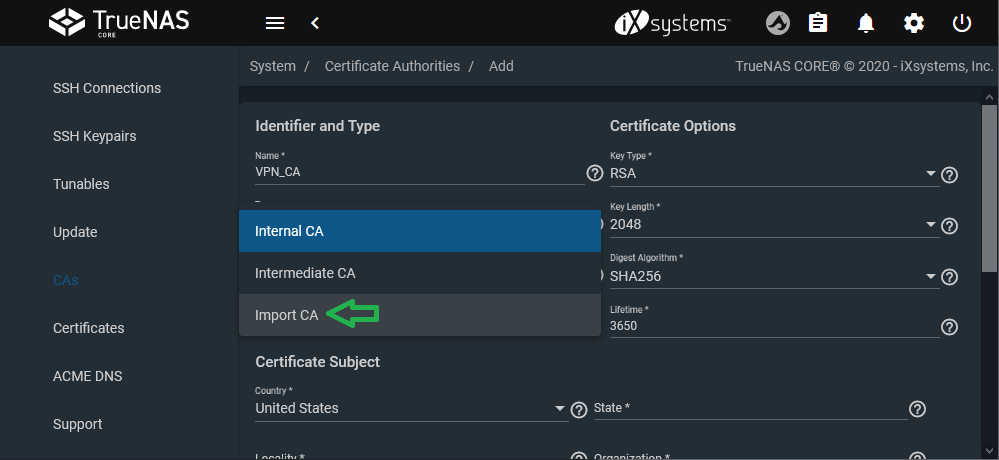
-
Copy and paste the certificate from the configuration file. The certificate is found between the tags
and of the OpenVPN config file. 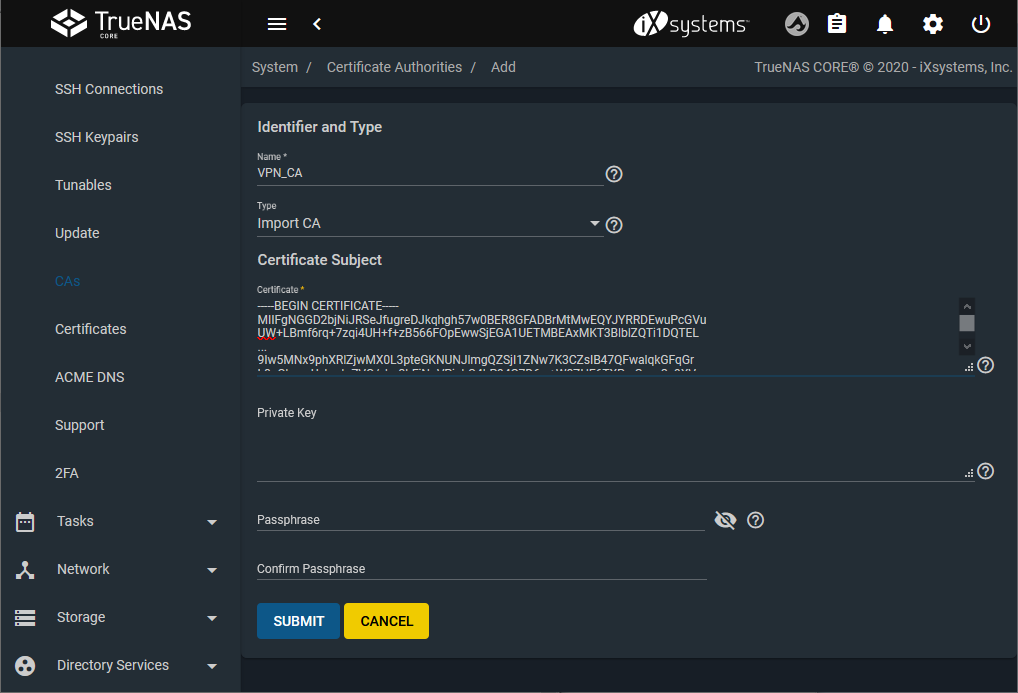
-
Open System > Certificate.
-
Add a certificate.
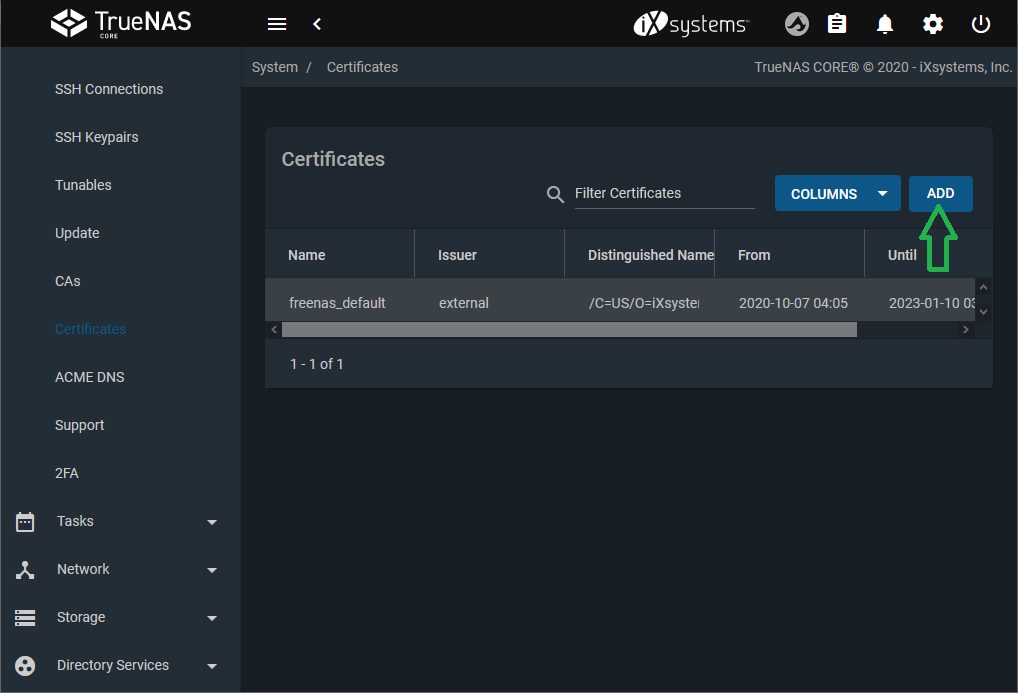
-
Give it a name (example:
VPN) and select Import Certificate as the Type. -
Copy and paste the certificate found in the OpenVPN config file between the tags
and . -
Copy and paste the key between the tags
and from the configuration file. 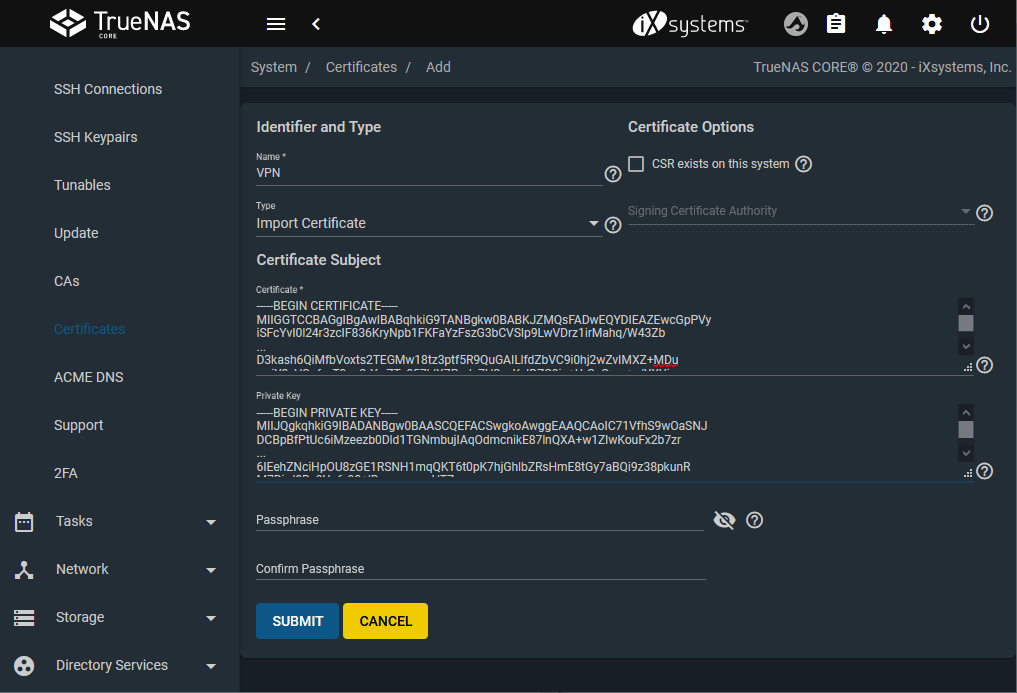
With a CA and Certificate created, we can configure the VPN connection next.
-
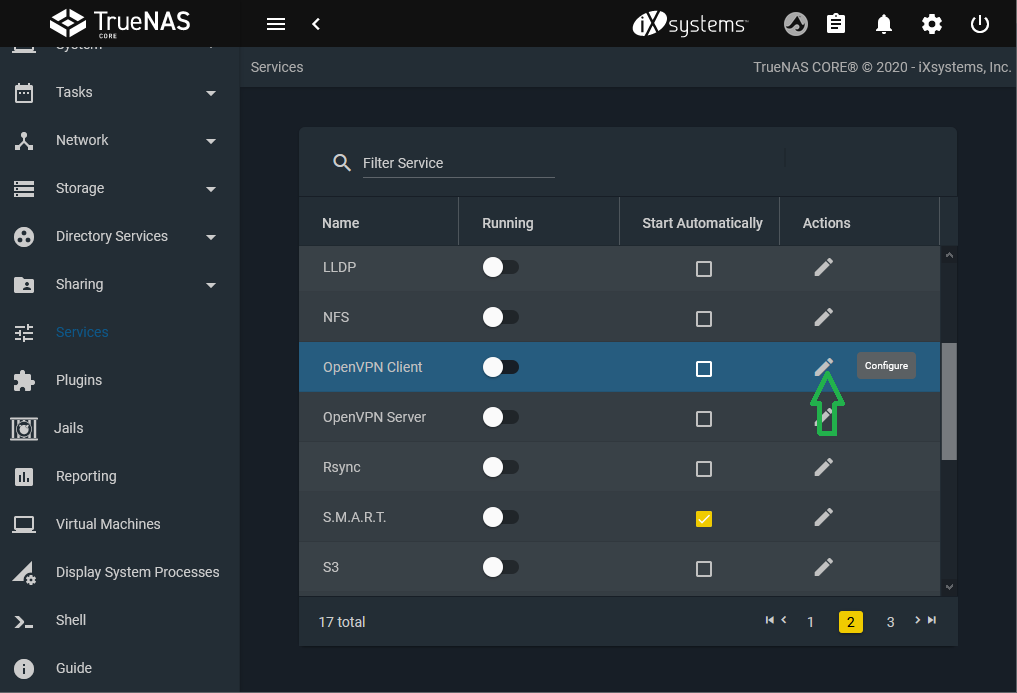
Go to the Services page and find the OpenVPN Client entry.
-
Click the to configure the service.
-
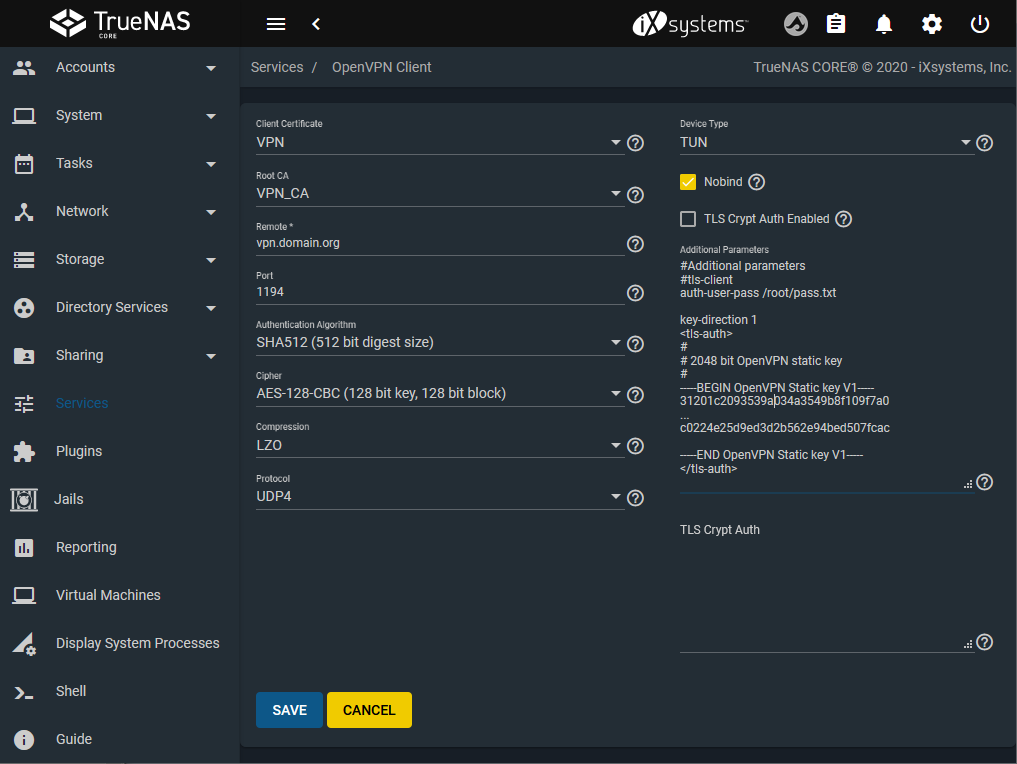
Choose the certificate and Root CA previously installed.
-
Port the remaining parameters found in the OpenVPN configuration file.
-
Additional parameters stores options from the configuration files, like the TLS key for authentication or user login/password.
-
Go to the Services page and find the OpenVPN service.
-
Toggle the service to start it. If desired, select the Start Automatically checkbox to have the service start each time the system boots.
-
Test if the connection is working using
curl ifconfig.mein a terminal. It returns the IP from the VPN connection and not from the local connection. Turn the OpenVPN client service on and off to see the difference.
Logs of the OpenVPN client are in /var/log/messages and /var/log/daemon.

